Belgian Security Researchers Find A Clunky But Effective Way To Steal A Tesla In Minutes
We may receive a commission on purchases made from links.
Here's a warning for Tesla owners: if you see a sort of Belgian-looking person (I assume that means they resemble TinTin?) walking around you and car, holding a box full of electronics and wires, maybe play it safe and smack the box out of their hands, then stomp on it. Because it's possible they could be part of COSIC, a research group from the University of Leuven in Belgium, that just discovered a huge security hole in Tesla Model S and X's keyless entry system that would allow the car to be stolen within minutes. That, or it could be some kind person bringing a video game console to some needy kids, and you're the jerk. Better not take a chance, though.
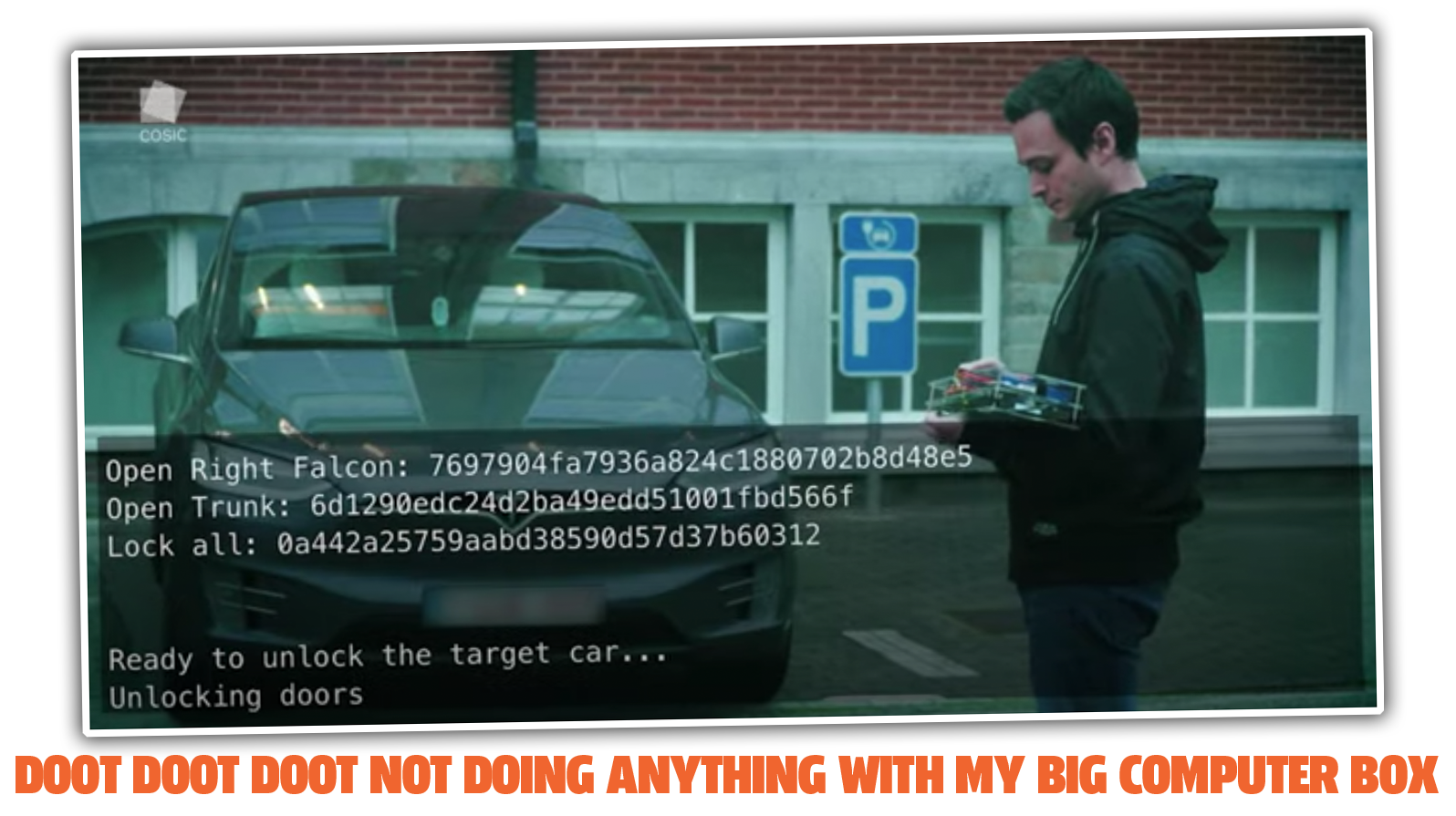
The security hole focuses on the Bluetooth Low Energy protocol that's used by Models S and X in their key fobs. Pulling off the exploit does require a bit of specialized hardware, specifically a modified Electronic Control Unit (it looks like it's the Body Control Module) salvaged from another Tesla combined with a Raspberry Pi computer, some interface items and a battery.
That's what the dude in the video is holding, nonchalantly, in this plexiglass box:
While out in broad daylight and in public and holding the thing all exposed like that looks pretty suspicious, there's no reason that hardware couldn't be slipped into a backpack or something and nobody would bat an eye. And while it seems like a lot of hardware for this, it's not like it's all that hard to get — the salvaged Tesla hardware looks to be about $136 on eBay and the Pi and other bits are pretty cheap; you could likely build that box for, oh, $300 or so? Maybe less.
Here's how the researchers broke down what they built:
The proof of concept attack was realized using a self-made device (see the video) built from inexpensive equipment: a Raspberry Pi computer ($35) with a CAN shield ($30), a modified key fob and ECU from a salvage vehicle ($100 on eBay) and a LiPo battery ($30).
And, here's a good encapsulation of what exactly that box was doing:
"To summarize, we can steal a Tesla Model X vehicle by first approaching a victim key fob within about 5 meters to wake up the key fob. Afterwards we can send our own software to the key fob in order to gain full control over it. This process takes 1.5 minutes but can be easily performed over a range of more than 30 meters. After compromising the key fob, we can obtain valid commands that will allow unlocking the target vehicle. After approaching the vehicle and unlocking it we can access the diagnostic connector inside the vehicle. By connecting to the diagnostic connector, we can pair a modified key fob to the car. The newly paired key fob allows us to then start the car and drive off. By exploiting these two weaknesses in the Tesla Model X keyless entry system we are thus able to steal the car in a few minutes", says Dr. Benedikt Gierlichs, researcher at COSIC.
So, the ECU-rig pings the nearby key fob, gets in contact, takes it over, gets the unlock commands, which are then sent to unlock the car, and once inside, the hacker can pair a new fob, and, boom, they've got your car.
The researchers did inform Tesla of this vulnerability, and Tesla has fixed the hole and released an over-the-air update, 2020.48, which all you Tesla Model S and X owners should install to avoid any Belgians from stealing your car with a box full of motherboards and wires.
(Thanks, Michael S!)