Security Researchers Hack A Tesla From A Drone
As the current microchip shortage has really, really reminded us, modern cars are packed full of computers. And, like anything packed full of computers, especially computers with multiple wireless connectivity options, cars can be hacked. This was demonstrated in dramatic fashion recently, when a pair of security researchers successfully hacked a Tesla Model 3. And they did it remotely from a drone, flying over the car.
The research and eventual successful hack was started as part of the Pwn2Own2020 hacking competition, but when coronavirus concerns temporarily tabled the automotive portion of the event, the researchers decided to continue, and reported their findings to Tesla's bug bounty program.
The group was able to gain control over Tesla (it was found to work on the Model 3 and all other Tesla Models, S, X, and Y) infotainment systems, which, while not providing access to any actual driving or semi-automated driving features, gave access to an alarming number of features of the car, including the ability to unlock doors, open doors (Model X powered doors), changing seat positions, driving and steering modes, playing music, HVAC and climate control functions, and more.
Before I get into some (admittedly watered-down) technical details of the hack, I want to calm down the hordes of picture-of-Elon's-face-taped-to-a-soiled-body-pillow hardcore Tesla fans: Tesla is a partner in these hacking competitions, the exploit was patched in October 2020, and the vulnerable components detected in this hack are very likely used in other automakers' cars, so, while it was a Tesla compromised here, that does not mean other manufacturers are not vulnerable as well.
So get a grip, fellas.
Okay, some details. The researchers who found the vulnerability are Ralf-Philipp Weinmann of Kunnamon and Benedikt Schmotzle of Comsecuris. The primary focus of the attack was a piece of Intel software called ConnMann, which is a common tool used to manage internet connections for Linux-based embedded systems. It's used in many automotive systems, across brands.
ConnMan can be accessed via WiFi, which makes it a good target for an attack. Here's how the researchers describe the overall process:
We exploit the fact that modern Tesla vehicles such as the Model 3 automatically connect to the "Tesla Service" WiFi, together with two vulnerabilities in two components of the ConnMan daemon, to gain remote code execution on the CID (Infotainment): a stack overflow in the DNS forwarder, and a stack infoleak in the DHCP component. Having control over ConnMan is much more powerful than most other non-root daemons on the CID, as it allows to shut down the firewall, change routing tables, and load and unload kernel modules 1 . For demonstration purposes, we shut down the firewall and send a message to the gateway to open the charge port of the car.
So, basically, they know Teslas will automatically connect to any wifi networks with the SSID "Tesla Service", and the passcode for this network can be found in the car's firmware, or, kind of alarmingly, on "random Twitter profiles." I guess that means this passphrase isn't the most secure.
Once connected, they were able to exploit some vulnerabilities in ConnMann, one of which, a stack overflow attack, is one that's been known about since the 1990s, yet still manages to be an issue on modern systems.
In a really, really, really dumbed-down way, you can think of it as shoving so much data in a particular slot of memory that it "spills" over into another slot, and if you control what's spilling over, you can change the contents of a part of memory you normally may not have access to, allowing you to change things you're not supposed to change.
Again, programmers out there, go easy on me, I'm trying to simplify it as much as I can. But I think that's generally the idea. Email Rory for corrections.
Once breached, the hackers have access to the infotainment system, which is where all the real mayhem can take place.
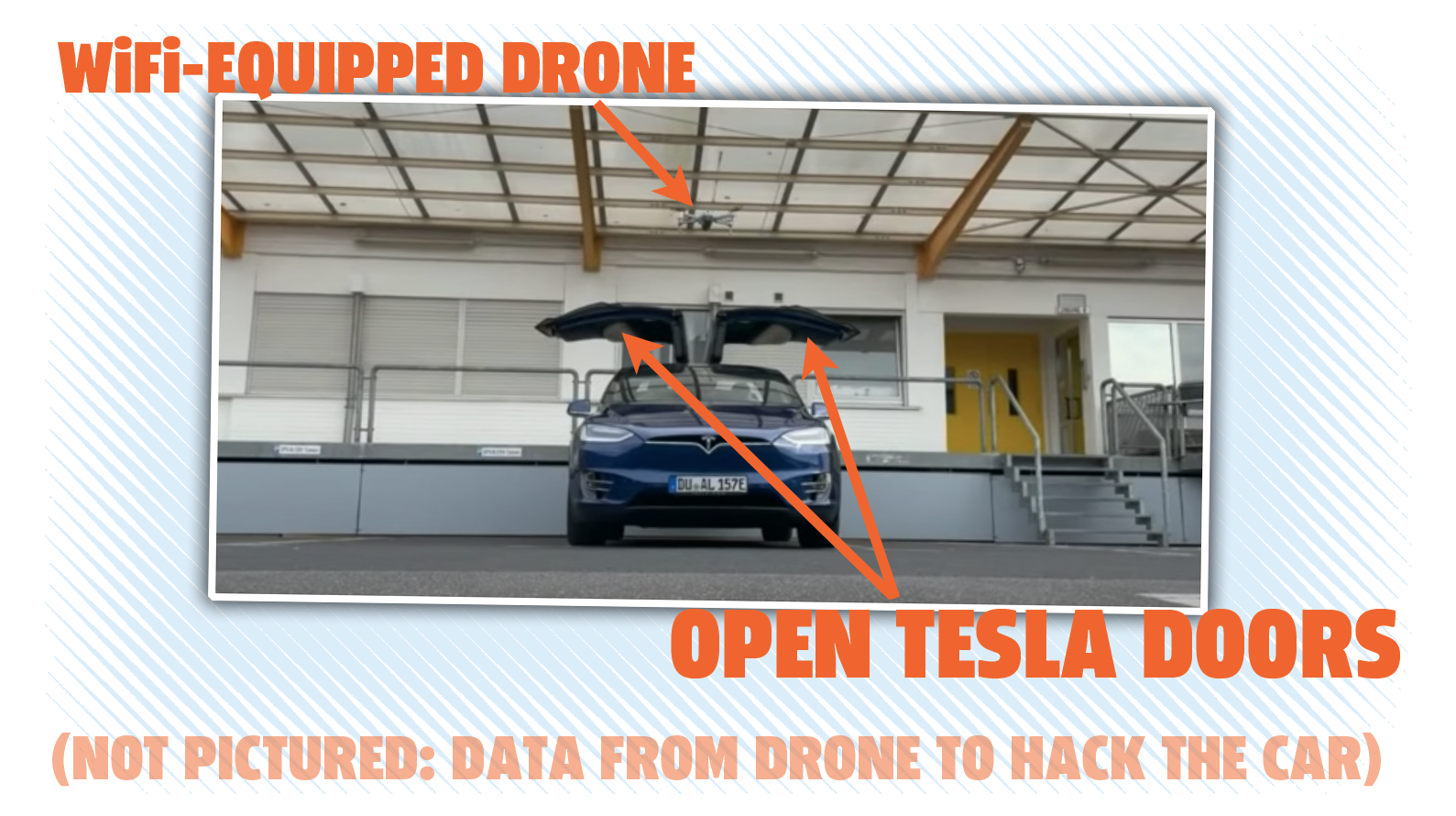
Because this is a completely remote hack that can take place over WiFi, that means a properly-equipped drone, buzzing around 300 feet above the car, can execute the attack. Which is what they did. Why do it this way?
The team addresses this in a slide:

It's fun. Hard to argue with that.
Full details of the exploit are available here. There's a video of their whole presentation as well, and I've queued it up to the video of their demonstration with the drone for you:
In the video there, you can see the view from the wifi-equipped drone's camera as it hovers over a Tesla Model X, and you can see the car open its falcon doors, triggered by a command from the drone.
As I said before, the issue has been fixed on Teslas, and Tesla has stopped using ConnMann and switched to software known as dnsmasq. Other carmakers would be wise to do the same.
Of course, this won't be the end of hacks and exploits of computers in cars; this is an on-going back-and-forth, and as long as there are people interested in hacking cars, there will be hacks, and then fixes, over and over, until we all become beings of pure thought or sex or smell or whatever.